Disaster recovery and business continuity
Atlassian actively plans for disruptions and implements redundancies in all products. Site Reliability Engineers monitor and test these regularly. Each Atlassian team has a Disaster Recovery Champion. These are specially trained employees who ensure that disaster recovery (DR) is integrated into projects. Regular DR testing improves processes and technologies.
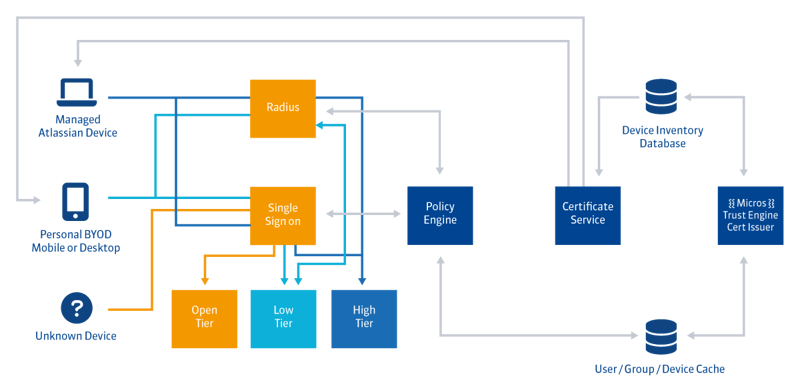
End-to-end data security at Atlassian
Industry-leading hosting infrastructure
Atlassian hosts its products and data on Amazon Web Services (AWS), a leading global cloud hosting provider. Customer data is stored in different geographical regions to avoid outages. Customers decide in which region or country their data is stored. Data centers in different availability zones replicate the data to ensure stability.
Control of data residency
Due to data protection regulations such as the GDPR, Atlassian enables its customers to control the storage locations of their data. The data residency feature allows IT administrators to tie user-created product information to specific data regions. This is currently supported in the European Union and the US, with plans to expand to other regions.
Atlassian provides comprehensive encryption for customer data and attachments in various products. Data at rest is encrypted with AES-256 and data transfers are done via TLS 1.2+ with Perfect Forward Secrecy to ensure security.
Working together to protect data
Atlassian takes responsibility for the security of its systems, but requires customer cooperation to protect data. There are shared responsibilities in the areas of policies, users and information. Third-party marketplace apps are reviewed and security standards such as Forge are offered.